Designed to develop capabilities that are essential to the effective performance of cybersecurity job roles, as well as helping to grow faculty and program capacity at 2/4-year schools.
Differentiator
Traditional workshops focus on exposure to new techniques, tools, and instructional materials (i.e., train-the-trainer) by conveying information about a topic. By contrast, the Cybersecurity Skills Development Workshops are designed to develop mastery in skillfully applying techniques, tactics, tools, protocols, or procedures through competency-based instructional designs. These workshops focus on developing understanding and practicing application under varying conditions or scenarios. CSDWs assist in raising the capability maturity and readiness of students, faculty, practitioners, or policymakers to adopt and adapt the latest effective practices for performing cybersecurity functions and roles.
CSDWs Apply Advances In
- Formative assessments, which are designed to detail the areas of strengths and weaknesses of the learner, as continually applied, and guide the next learning path.
- Adaptive learning systems, to ensure the achievement of mastery in understanding, applying, and adapting cybersecurity practices.
- Micro-credentialing, to recognize the level of capability maturity exhibited by the workshop participant as Proficient, Competent, or a Master of the new capability.
Workshop Formats
Ranging from:
- Half-day
- One-day
- Two-day workshops focused on a single capability, to
- Multi-week virtual and physical boot camps
Hands-On Cryptography Workshop
This Workshop took place in-person on July 30, 2019 from 9am-5pm at the annual Community College Cyber Summit at host institution Bossier Parish Community College, LA, and provided an in-depth look at both classical and modern cryptographic techniques.
Goals: Provide participants with an IT/operations-based approach to securing information both at rest and in-transit.
Target Audience: Educators at two- and four-year colleges/universities teaching the following courses/topics: Cisco Networking Academy, CompTIA Security+, Information Systems Security, Network Security, Systems Administration, VPNs.
Workshop Topics:
- Classical cryptographic techniques: 1 hour
- Fundamentals of modern cryptographic algorithms: 5 hours
- Common implementations: 1 hour
- Common attacks against encrypted data: 1 hour
Workshop Format: The Workshop was taught in both lecture and hands-on formats. Upon completion of the CSDW, participants received all the instructional materials (lecture slides, hands-on lab exercises) and guidance on how to incorporate them into their classes.
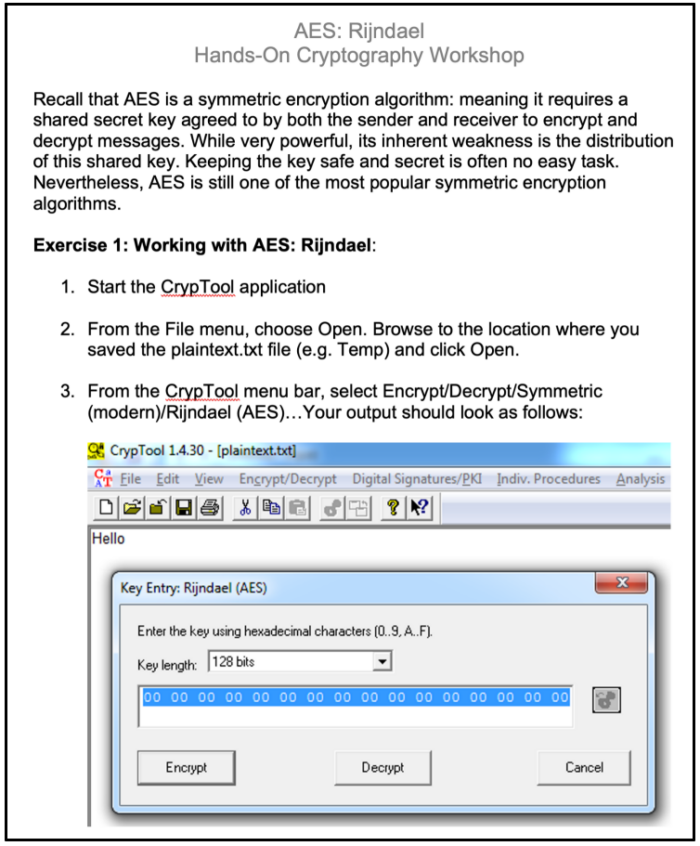
Fig. 1: Sample hands-on lab exercise
Formative Assessments: Participants had a chance to implement the topics in various hands-on exercises throughout the Workshop. In addition, all participants completed a pre/post survey that combined demographic and fill-in-the-blank questions. Participants were provided with their assessment results that classified each respondent into the following categories: Novice, Beginner, Developing Expertise, Nearly Proficient, Proficient, and Master.
Micro-Credential: Participants that completed the Workshop (and related exercises and assessments) received a badge (see below). The metadata embedded in the badge included the date of the workshop, the issuer, and the following concepts that were covered in detail (NOTE: these concepts were mapped to the National Institute of Standards and Technology (NIST) Special Publication 800-181 version 1: The Workforce Framework for Cybersecurity (NICE Framework) Knowledge IDs, as well as the National Security Agency (NSA)/Dept. of Homeland Security (DHS) National Centers of Academic Excellence in Cybersecurity (NCAE-C) Knowledge Units:
Access Control, Algorithm, Asymmetric Algorithms, Asymmetric Cryptography, Authentication, Benefits of Cryptography, Block Cipher, Boolean Math, Ciphertext, Classical Cryptography, Collision, Confidentiality, Cryptanalysis, Cryptographic Algorithms, Cryptography, Cryptology, Cryptosystem, Data-at-Rest, Decryption, Decryption Algorithms, Digital Signature, Encryption, Encryption Algorithms, Hash Function, Hash Value, Hashing Algorithms, Integrity, Key, Key Escrow, Key Management, Key Pair, Message Digest (MD), Nonrepudiation, One-Way Function, OR, Plaintext, Private Key, Pseudorandom Number Generators (PRNG), Public Key, Public Key Cryptography, Public Key Infrastructure (PKI), Randomness, Secure Hash Algorithm (SHA), Session Key, Shared Key, Stream Cipher, Symmetric Algorithms, Symmetric Cryptography, Symmetric vs. Asymmetric Cryptography, XOR.
Fig 2: Badge issued upon successful completion of CSDW

Contact Us
For more information, contact us at info@nationalcyberwatch.org
